Difference between revisions of "Network Questions"
(Created page with "<div id="FileServer"></div> == What network storage is available to me? == All CIS users have storage on the department file server. Anything you place in your home directory...") |
(→Putty) |
||
| (38 intermediate revisions by 3 users not shown) | |||
| Line 2: | Line 2: | ||
== What network storage is available to me? == | == What network storage is available to me? == | ||
| − | All | + | All CS users have ''home directory'' on the department file server to store files. Anything you place in your home directory is backed up nightly, with revisions stored going back six months. |
| − | On department linux systems, your home directory is automatically mounted as $HOME. The full path | + | === Linux Systems === |
| − | < | + | On department linux systems, your home directory is automatically mounted as <code>$HOME</code>. The full path of your home directory can be found using the <code>finger</code> command on any linux host. |
| − | + | <nowiki> | |
| − | + | finger testacct | |
| − | + | Login: testacct Name: Testing Tester | |
| − | + | Directory: /home/t/testacct Shell: /bin/bash | |
| − | + | Never logged in. | |
| − | + | No mail. | |
| − | </ | + | No Plan.</nowiki> |
| − | |||
| − | + | In this case, testacct's home directory is <code>/home/t/testacct</code>. | |
| − | If you need a large amount of space temporarily, you can request space in the transient volume (send an email to help@ | + | === Windows Systems === |
| + | On department Windows systems, your home directory should be mounted as the U:\ drive. If you are manually mounting a drive, use the URI <code>\\files.cs.ksu.edu\<username></code> where <code><username></code> is your eID. | ||
| + | |||
| + | <div id="Transient"></div> | ||
| + | == Transient Storage == | ||
| + | If you need a large amount of space temporarily, you can request space in the transient volume (send an email to [mailto:help@cs.ksu.edu help@cs.ksu.edu]). There are no quotas on directories in this volume, but there are also no backups made of files here. Support staff may also ask you to clean files out periodically to make room for others. On department linux systems, your transient directory will be found in <code>/transient/<username></code>. On department Windows systems, you can mount the share <code>\\files.cs.ksu.edu\transient\<username></code> to a drive letter of your choosing. | ||
== How do I setup CGI on my web page? == | == How do I setup CGI on my web page? == | ||
| − | + | Please see the page on [[Personal Web Pages]]. | |
| − | |||
== Why don't you have an FTP server? == | == Why don't you have an FTP server? == | ||
| Line 28: | Line 31: | ||
FTP is a ''very'' old protocol. It was designed before security considerations were a major part of protocol design. As such, passwords to the FTP server are sent in plain text---any clever user on the network can snoop your packets and steal your password. This would allow that user to gain access to your account, which is an unacceptable violation of our security. | FTP is a ''very'' old protocol. It was designed before security considerations were a major part of protocol design. As such, passwords to the FTP server are sent in plain text---any clever user on the network can snoop your packets and steal your password. This would allow that user to gain access to your account, which is an unacceptable violation of our security. | ||
| − | If you need to access your home directory from a remote location, there are two different methods for doing so. See the documentation in the | + | If you need to access your home directory from a remote location, there are two different methods for doing so. See the documentation in the CS Systems UserGuide for Remote Access or in the FrequentlyAskedQuestions about how to access your home directory from a non-CS computer. |
== How do I use HTTP authentication? == | == How do I use HTTP authentication? == | ||
| Line 35: | Line 38: | ||
follow these steps from a linux shell (you will want to change <code>passwordProtectedDir</code> to whatever name you want and use your own usernames). <code><your_home_dir_path></code> is the full path to your home directory. If you don't know what this is, use the finger command from the command prompt of any linux host ("<code>finger <eid></code>", where <code><eid></code> is your eID). | follow these steps from a linux shell (you will want to change <code>passwordProtectedDir</code> to whatever name you want and use your own usernames). <code><your_home_dir_path></code> is the full path to your home directory. If you don't know what this is, use the finger command from the command prompt of any linux host ("<code>finger <eid></code>", where <code><eid></code> is your eID). | ||
| − | < | + | <nowiki> |
| − | + | cd ~/public_html/ | |
| − | + | mkdir passwordProtectedDir | |
| − | + | cd passwordProtectedDir | |
| − | + | htpasswd -c .htpasswd user_who_gets_access | |
| − | + | htpasswd .htpasswd other_user | |
| − | + | cat << EOF > ~/public_html/passwordProtectedDir/.htaccess | |
| − | + | AuthType Basic | |
| − | + | AuthName "Checking Password" | |
| − | + | AuthUserFile <your_home_dir_path>/public_html/passwordProtectedDir/.htpasswd | |
| − | + | Require valid-user | |
| − | + | EOF</nowiki> | |
| − | </ | ||
Now create any files you want in the directory and set permissions appropriately. | Now create any files you want in the directory and set permissions appropriately. | ||
| − | < | + | <nowiki> |
| − | + | chmod o+rx ~/public_html/passwordProtectedDir | |
| − | + | chmod o+r ~/public_html/passwordProtectedDir/*.*</nowiki> | |
| − | </ | ||
| − | If you would like your files to only be password protected off-campus, use | + | If you would like your files to only be password protected off-campus, use this command to make your htaccess file. |
| − | this command to make your htaccess file. | ||
| − | < | + | <nowiki> |
| − | + | cat << EOF > ~/public_html/passwordProtectedDir/.htaccess | |
| − | + | AuthType Basic | |
| − | + | AuthName "Checking Password" | |
| − | + | AuthUserFile <your_home_dir_path>/public_html/passwordProtectedDir/.htpasswd | |
| − | + | Require valid-user | |
| − | + | Order Allow,Deny | |
| − | + | # This restricts access without a password to the KSU network | |
| − | + | Allow from 12# 130.0.0/16 | |
| − | + | # This restricts access without a password to the CS network | |
| − | + | #Allow from 12# 130.8.0/22 | |
| − | + | Satisfy any | |
| − | + | EOF</nowiki> | |
| − | </ | ||
== Why am I getting 500 Interal Server Error on all my scripts? == | == Why am I getting 500 Interal Server Error on all my scripts? == | ||
| Line 83: | Line 82: | ||
<li>Your script must be stored in your home directory in the subdirectory named <code>public_html/cgi-bin</code>. You cannot place your scripts anywhere else.</li> | <li>Your script must be stored in your home directory in the subdirectory named <code>public_html/cgi-bin</code>. You cannot place your scripts anywhere else.</li> | ||
<li>You must make sure that your home directory, the <code>public_html</code> directory, and the <code>cgi-bin</code> directory are not group or other writable:</li> | <li>You must make sure that your home directory, the <code>public_html</code> directory, and the <code>cgi-bin</code> directory are not group or other writable:</li> | ||
| − | |||
chmod 755 ~ | chmod 755 ~ | ||
chmod 755 ~/public_html | chmod 755 ~/public_html | ||
chmod 755 ~/public_html/cgi-bin | chmod 755 ~/public_html/cgi-bin | ||
| − | |||
<li> Finally, you must make sure your scripts are executable, but not group or other writable:</li> | <li> Finally, you must make sure your scripts are executable, but not group or other writable:</li> | ||
| − | |||
chmod 755 ~/public_html/cgi-bin/my-script.cgi | chmod 755 ~/public_html/cgi-bin/my-script.cgi | ||
| − | |||
<li> If you have problems, try checking the end of the logs for additional information while pressing reload on your browser:</li> | <li> If you have problems, try checking the end of the logs for additional information while pressing reload on your browser:</li> | ||
| − | |||
tail -f /web/logs/error_log /web/logs/suexec_log | tail -f /web/logs/error_log /web/logs/suexec_log | ||
| − | |||
</ol> | </ol> | ||
| Line 103: | Line 96: | ||
<li>Your script must be stored in your home directory under the directory named <code>public_html</code> or a subdirectory of that directory.</li> | <li>Your script must be stored in your home directory under the directory named <code>public_html</code> or a subdirectory of that directory.</li> | ||
<li>You must make sure that your home directory, the <code>public_html</code> directory, and every directory above your PHP script is accessible but not group or other writable:</li> | <li>You must make sure that your home directory, the <code>public_html</code> directory, and every directory above your PHP script is accessible but not group or other writable:</li> | ||
| − | |||
chmod 755 ~ | chmod 755 ~ | ||
chmod 755 ~/public_html | chmod 755 ~/public_html | ||
chmod 755 ~/public_html/otherdir | chmod 755 ~/public_html/otherdir | ||
| − | |||
<li>Finally, you must make sure your scripts are readable, but not group or other writable:</li> | <li>Finally, you must make sure your scripts are readable, but not group or other writable:</li> | ||
| − | |||
chmod 644 ~/public_html/index.php | chmod 644 ~/public_html/index.php | ||
chmod 644 ~/public_html/otherdir/index.php | chmod 644 ~/public_html/otherdir/index.php | ||
| − | |||
<li>If you have problems, try checking the end of the logs for additional information while pressing reload on your browser:</li> | <li>If you have problems, try checking the end of the logs for additional information while pressing reload on your browser:</li> | ||
| − | |||
tail -f /common/weblogs/polara/error.log /common/weblogs/polara/suphp.log | tail -f /common/weblogs/polara/error.log /common/weblogs/polara/suphp.log | ||
| − | |||
</ol> | </ol> | ||
== How do I setup ssh keys? == | == How do I setup ssh keys? == | ||
| − | + | ===Linux/MacOS & Powershell=== | |
| − | follow | + | Note: If you can run the command <code>ssh-keygen.exe</code> in powershell without receiving an error you can follow these instructions, just be sure to replace any "~" with "$HOME" and "/" with "\" when you seem them. Otherwise follow the putty instructions below. |
| + | <ol> | ||
| + | <li>Open a terminal and run the command <code>ssh-keygen -t rsa</code>.</li> | ||
| + | <li>You will be asked to specify the keys file path, the default will likely be<code>/home/username/.ssh/id_rsa </code>. If you specify a different path it must be global.</li> | ||
| + | <li>Next you will be asked for a password to encrypt your key with. If you don't want to encrypt your key you can leave the filed blank and press enter, if you use a password it should be different from your users password. </li> | ||
| + | <li> There should now be two new files <code>id_rsa</code> and <code>id_rsa.pub</code>in the folder <code>~/.ssh/</code>. (This document will assume you used default file paths)</li> | ||
| + | <li>Next you will need to run the command <code>ssh-copy-id -i ~/.ssh/id_rsa.pub username@cslinux.cs.ksu.edu</code>, you will be prompted for your password and after that you should be done. If you have issues with this command you can follow step 5, otherwise you can skip to step 6.</li> | ||
| + | <li>You will need to copy the contents of your public key (the .pub file) from your local machine into the file <code>~/.ssh/authorized_keys</code> on the server you want to ssh into, this should just be one long string on a single line. You can use scp to copy the file over and append it to the authorized_keys file, or you can copy it to your clipboard and paste it with a text editor.</li> | ||
| + | <li>With your public key copied over as long as you have your private key in the folder <code>~/.ssh/</code>. Close and reopen your terminal and you should be able to login as normal but without entering your password, or only entering your specified decryption password.</li> | ||
| + | <li>If you gave your key a non default path you will need to tell your SSH client where to find your key by editing or creating the file <code>~/.ssh/config</code> and adding the line <code> IdentityFile /path/to/private_key</code>. For more information on SSH client configurations check the man page for <code>ssh_config</code>.</li> | ||
| + | </ol> | ||
| − | + | ===Putty=== | |
| − | + | To set up ssh keys on windows hosts first make sure you have both putty and puttygen installed [https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html here]. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <ol> | |
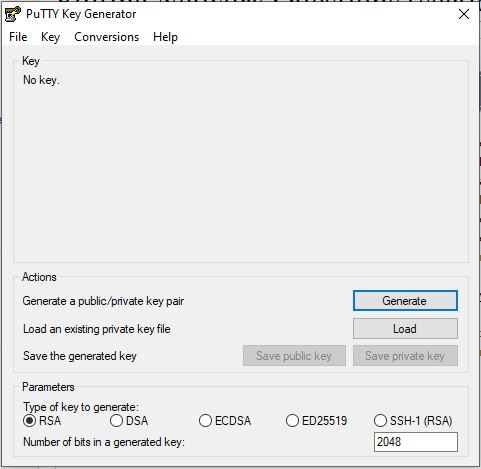
| − | + | <li>Open puttygen, make sure RSA is selected at the bottom and click generate. | |
| − | + | <p>[[File:puttygen.JPG]]</li> | |
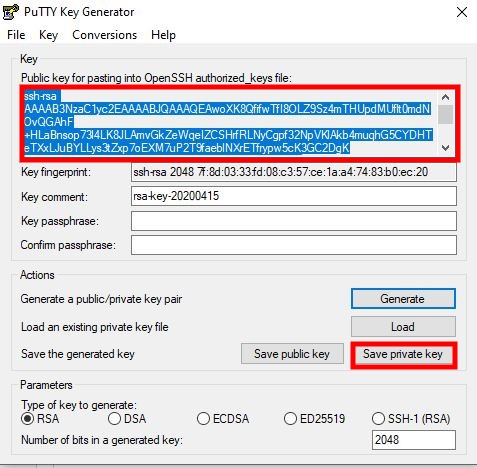
| + | <li>Click Save private key and click yes when it asks if its okay to create a key without a password. Put this file away somewhere (Do not just drop it on your desktop).</li> | ||
| + | <li>Then select everything in the text box labeled "Public key for pasting into OpenSSH authorized_key file" and copy it to a file somewhere near your private key. | ||
| + | <p>[[File:Puttygenerated.jpg]] | ||
| + | <p> | ||
| + | You are done working on your windows host for now, you will need to ssh into the machine you want to set up keys on.</li> | ||
| + | <li>Open the file <code>~/.ssh/authorized_keys</code> (if this file doesn't exist you can make it). The key should just be one very long string on a single line.</li> | ||
| + | <li>Run the commands <code>chmod 700 ~/.ssh/</code> and <code>chmod 600 ~/.ssh/authorized_keys</code> | ||
| + | You are now done setting up the keys and you can log out of this machine. The only thing you need to do from here on is specify which private key to use next time you log on.</li> | ||
| + | <li>Open putty and select auth under the ssh drop down on the left.</li> | ||
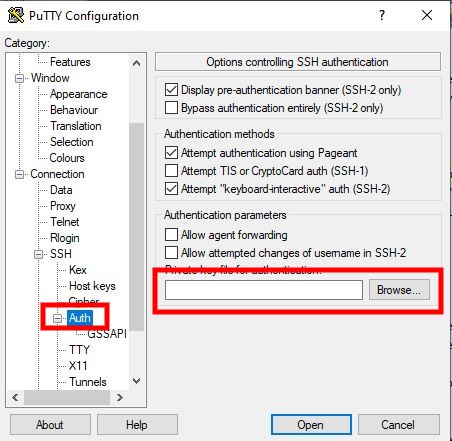
| + | <li>Select browse at the bottom of the list and navigate to you the .ppk file you made in step 2 | ||
| + | <p>[[File:SelectKeys.jpg]]</li> | ||
| + | <li>Return to the session tab on the left, enter the address of the machine you want to connect to and click the open button.</li> | ||
| + | <li>You should be prompted for your username but you should not need to type your password and you should be authenticated.</li> | ||
| + | </ol> | ||
== How do I access the campus VPN? == | == How do I access the campus VPN? == | ||
| − | + | See [[:Remote_Access#Access_Through_Campus_VPN | Access Through Campus VPN]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | == How do I login remotely to CS resources? == | |
| − | + | See [[Remote Access]] | |
Latest revision as of 17:12, 9 March 2022
What network storage is available to me?
All CS users have home directory on the department file server to store files. Anything you place in your home directory is backed up nightly, with revisions stored going back six months.
Linux Systems
On department linux systems, your home directory is automatically mounted as $HOME. The full path of your home directory can be found using the finger command on any linux host.
finger testacct Login: testacct Name: Testing Tester Directory: /home/t/testacct Shell: /bin/bash Never logged in. No mail. No Plan.
In this case, testacct's home directory is /home/t/testacct.
Windows Systems
On department Windows systems, your home directory should be mounted as the U:\ drive. If you are manually mounting a drive, use the URI \\files.cs.ksu.edu\<username> where <username> is your eID.
Transient Storage
If you need a large amount of space temporarily, you can request space in the transient volume (send an email to help@cs.ksu.edu). There are no quotas on directories in this volume, but there are also no backups made of files here. Support staff may also ask you to clean files out periodically to make room for others. On department linux systems, your transient directory will be found in /transient/<username>. On department Windows systems, you can mount the share \\files.cs.ksu.edu\transient\<username> to a drive letter of your choosing.
How do I setup CGI on my web page?
Please see the page on Personal Web Pages.
Why don't you have an FTP server?
FTP is a very old protocol. It was designed before security considerations were a major part of protocol design. As such, passwords to the FTP server are sent in plain text---any clever user on the network can snoop your packets and steal your password. This would allow that user to gain access to your account, which is an unacceptable violation of our security.
If you need to access your home directory from a remote location, there are two different methods for doing so. See the documentation in the CS Systems UserGuide for Remote Access or in the FrequentlyAskedQuestions about how to access your home directory from a non-CS computer.
How do I use HTTP authentication?
To setup password authentication for a directory in your personal web space
follow these steps from a linux shell (you will want to change passwordProtectedDir to whatever name you want and use your own usernames). <your_home_dir_path> is the full path to your home directory. If you don't know what this is, use the finger command from the command prompt of any linux host ("finger <eid>", where <eid> is your eID).
cd ~/public_html/ mkdir passwordProtectedDir cd passwordProtectedDir htpasswd -c .htpasswd user_who_gets_access htpasswd .htpasswd other_user cat << EOF > ~/public_html/passwordProtectedDir/.htaccess AuthType Basic AuthName "Checking Password" AuthUserFile <your_home_dir_path>/public_html/passwordProtectedDir/.htpasswd Require valid-user EOF
Now create any files you want in the directory and set permissions appropriately.
chmod o+rx ~/public_html/passwordProtectedDir chmod o+r ~/public_html/passwordProtectedDir/*.*
If you would like your files to only be password protected off-campus, use this command to make your htaccess file.
cat << EOF > ~/public_html/passwordProtectedDir/.htaccess AuthType Basic AuthName "Checking Password" AuthUserFile <your_home_dir_path>/public_html/passwordProtectedDir/.htpasswd Require valid-user Order Allow,Deny # This restricts access without a password to the KSU network Allow from 12# 130.0.0/16 # This restricts access without a password to the CS network #Allow from 12# 130.8.0/22 Satisfy any EOF
Why am I getting 500 Interal Server Error on all my scripts?
We use programs named suexec and suphp to make sure that all of your scripts run as you. This allows your scripts to access files that would normally be private and inaccessible by the web server. However, for security these programs will not allow your scripts to run unless the permissions set on your files and on the directories containing them are safe.
For CGI scripts, you must make sure the following are true:
- Your script must be stored in your home directory in the subdirectory named
public_html/cgi-bin. You cannot place your scripts anywhere else. - You must make sure that your home directory, the
public_htmldirectory, and thecgi-bindirectory are not group or other writable:
chmod 755 ~
chmod 755 ~/public_html
chmod 755 ~/public_html/cgi-bin
- Finally, you must make sure your scripts are executable, but not group or other writable: chmod 755 ~/public_html/cgi-bin/my-script.cgi
- If you have problems, try checking the end of the logs for additional information while pressing reload on your browser: tail -f /web/logs/error_log /web/logs/suexec_log
For PHP scripts, you must make sure the following are true:
- Your script must be stored in your home directory under the directory named
public_htmlor a subdirectory of that directory. - You must make sure that your home directory, the
public_htmldirectory, and every directory above your PHP script is accessible but not group or other writable:
chmod 755 ~
chmod 755 ~/public_html
chmod 755 ~/public_html/otherdir
- Finally, you must make sure your scripts are readable, but not group or other writable: chmod 644 ~/public_html/index.php chmod 644 ~/public_html/otherdir/index.php
- If you have problems, try checking the end of the logs for additional information while pressing reload on your browser: tail -f /common/weblogs/polara/error.log /common/weblogs/polara/suphp.log
How do I setup ssh keys?
Linux/MacOS & Powershell
Note: If you can run the command ssh-keygen.exe in powershell without receiving an error you can follow these instructions, just be sure to replace any "~" with "$HOME" and "/" with "\" when you seem them. Otherwise follow the putty instructions below.
- Open a terminal and run the command
ssh-keygen -t rsa. - You will be asked to specify the keys file path, the default will likely be
/home/username/.ssh/id_rsa. If you specify a different path it must be global. - Next you will be asked for a password to encrypt your key with. If you don't want to encrypt your key you can leave the filed blank and press enter, if you use a password it should be different from your users password.
- There should now be two new files
id_rsaandid_rsa.pubin the folder~/.ssh/. (This document will assume you used default file paths) - Next you will need to run the command
ssh-copy-id -i ~/.ssh/id_rsa.pub username@cslinux.cs.ksu.edu, you will be prompted for your password and after that you should be done. If you have issues with this command you can follow step 5, otherwise you can skip to step 6. - You will need to copy the contents of your public key (the .pub file) from your local machine into the file
~/.ssh/authorized_keyson the server you want to ssh into, this should just be one long string on a single line. You can use scp to copy the file over and append it to the authorized_keys file, or you can copy it to your clipboard and paste it with a text editor. - With your public key copied over as long as you have your private key in the folder
~/.ssh/. Close and reopen your terminal and you should be able to login as normal but without entering your password, or only entering your specified decryption password. - If you gave your key a non default path you will need to tell your SSH client where to find your key by editing or creating the file
~/.ssh/configand adding the lineIdentityFile /path/to/private_key. For more information on SSH client configurations check the man page forssh_config.
Putty
To set up ssh keys on windows hosts first make sure you have both putty and puttygen installed here.
- Open puttygen, make sure RSA is selected at the bottom and click generate.
- Click Save private key and click yes when it asks if its okay to create a key without a password. Put this file away somewhere (Do not just drop it on your desktop).
- Then select everything in the text box labeled "Public key for pasting into OpenSSH authorized_key file" and copy it to a file somewhere near your private key.
You are done working on your windows host for now, you will need to ssh into the machine you want to set up keys on.
- Open the file
~/.ssh/authorized_keys(if this file doesn't exist you can make it). The key should just be one very long string on a single line. - Run the commands
chmod 700 ~/.ssh/andchmod 600 ~/.ssh/authorized_keysYou are now done setting up the keys and you can log out of this machine. The only thing you need to do from here on is specify which private key to use next time you log on. - Open putty and select auth under the ssh drop down on the left.
- Select browse at the bottom of the list and navigate to you the .ppk file you made in step 2
- Return to the session tab on the left, enter the address of the machine you want to connect to and click the open button.
- You should be prompted for your username but you should not need to type your password and you should be authenticated.
How do I access the campus VPN?
How do I login remotely to CS resources?
See Remote Access